Use of Company Assets
-

Working remotely? Protect your data!
Your employees likely work on the go—from hotels, airports, home, bathroom stalls (hey, we don’t judge!)—which invites increased cybersecurity, privacy, and confidentiality risks. Kick your worries to the curb by giving them this tool,...
View8✨ -
 🔥 Trending
🔥 TrendingYou are responsible for what you know - horizontal
Keep your Code of Conduct top-of-mind and aligned with everyday tasks with this graphic. Even better? It's part of an entire system: use it with our Annual Refresher Course and Basic Code of Conduct Obligations infographic for a...
View2✨ -

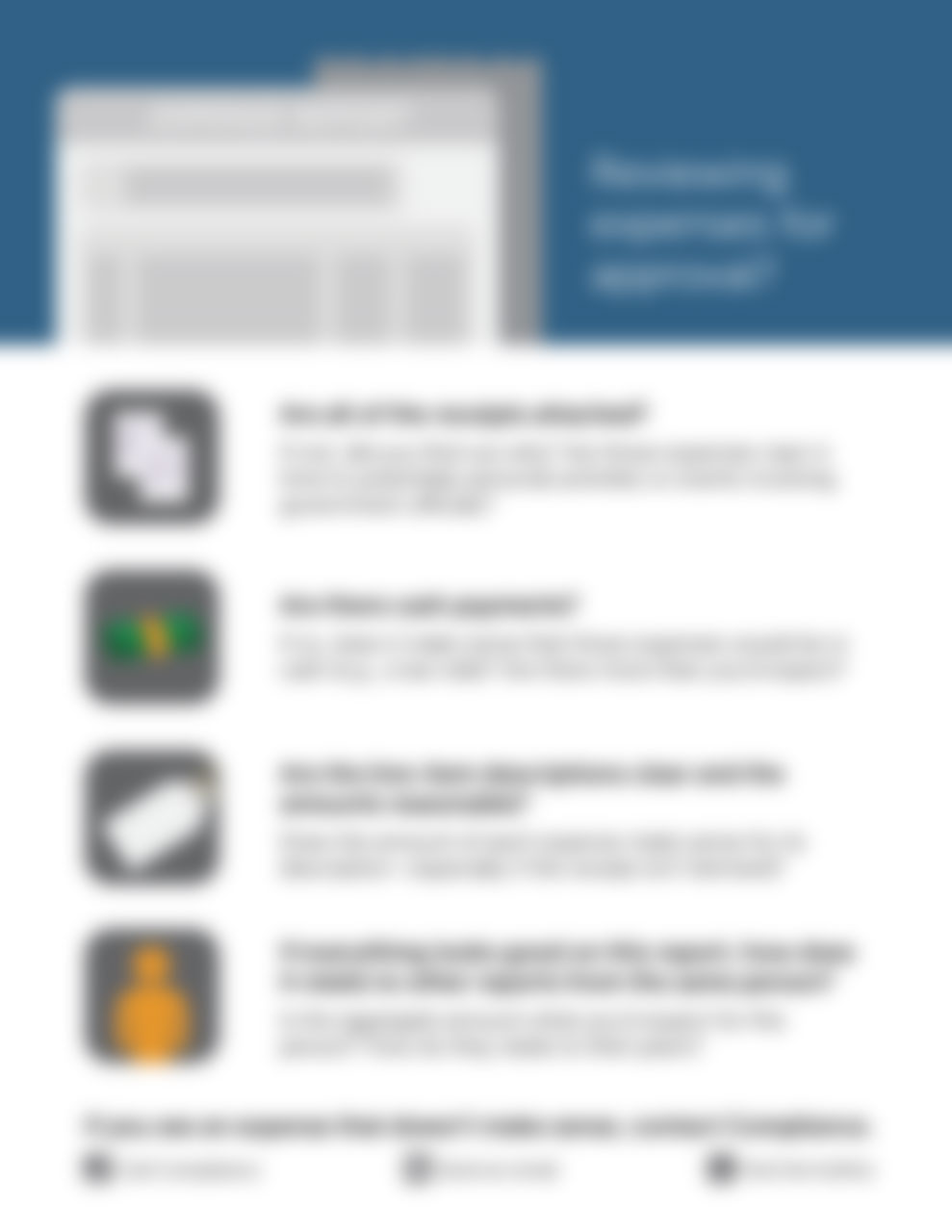
Expense approval checklist
Give your team an easy-to-understand checklist for walking through the major issues when approving expense reports. Proper approval of expenses requires thoughtful reflection about what, exactly, your organization is paying for—something not...
View8✨ -

Notify Privacy when mistakes happen
Being accountable and fixing mistakes yourself is great, but when it comes to privacy mishaps, there are situations where the Privacy Team needs to be looped in. This infographic explains the most common scenarios that require their helping...
View6✨ -

Careful virtual communications
We may love dishing about juicy binge-worthy shows on Slack, but it’s easy to forget that these types of communications are on company record, which can lead to problems if discussions take a sensitive turn. At best: cringey embarrassing...
View8✨ -
 🔥 Trending
🔥 TrendingTravel & expense red flags checklist
Stop fraud and corruption risks in their tracks with this thorough checklist for reviewing T&E reports. Help your managers externalize their memory of procedures and red flags with this piece—they can focus on the harder questions when they...
View8✨ -

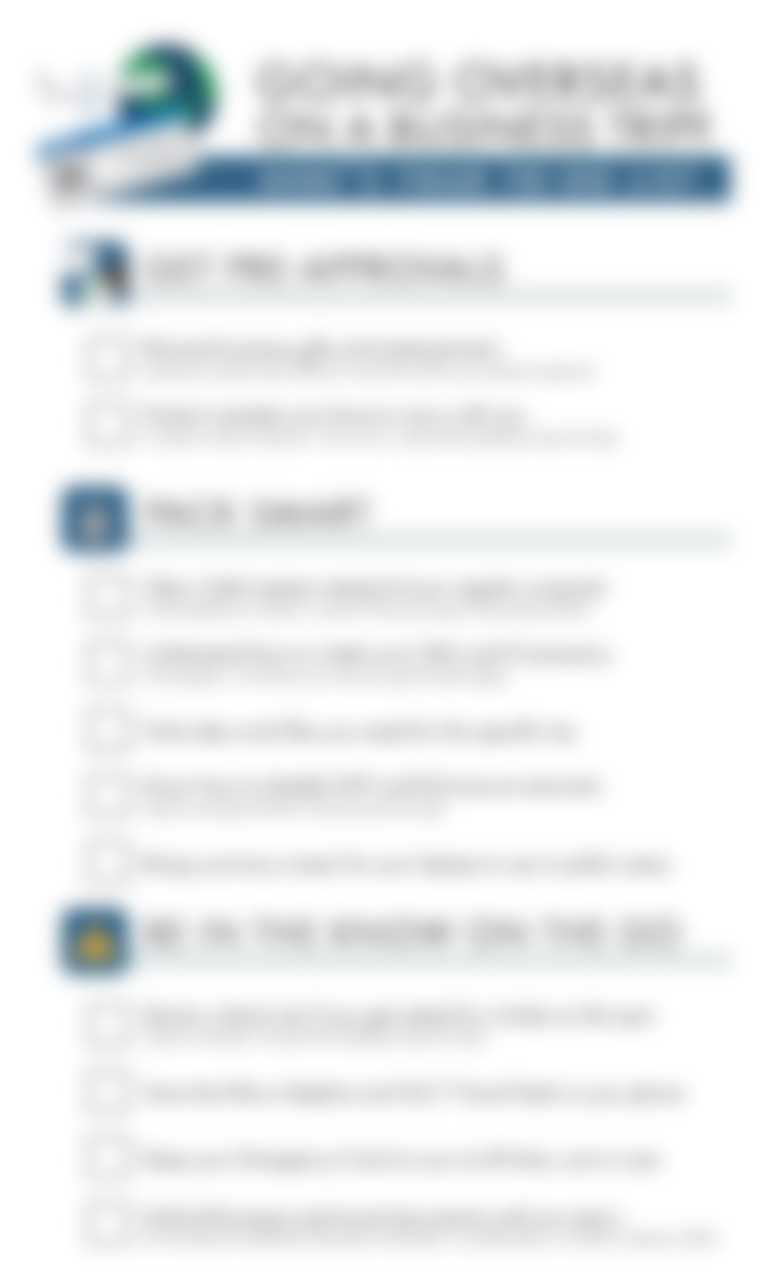
Going on a business trip? (Overseas travel checklist)
This piece is famous for a reason! These simple to-do's prepare your international travelers how to be safe and ethical abroad, without getting mired in legal details. This checklist covers the trade control, cybersecurity, privacy, anticorruption,...
View8✨ -

When should I contact the Privacy Team?
Living your values means ensuring data privacy throughout your org. You’ve written all the policies, operationalized training, and have a Chief Privacy Officer. But do your people know when to pick up the phone and contact the Privacy Team? This...
View8✨ -

You're free to participate in political activities - horizontal
It's easy to get carried away during election season. Remind your team that when they're speaking up, they're speaking on behalf of themselves (and using their own resources when doing so).
View2✨ -

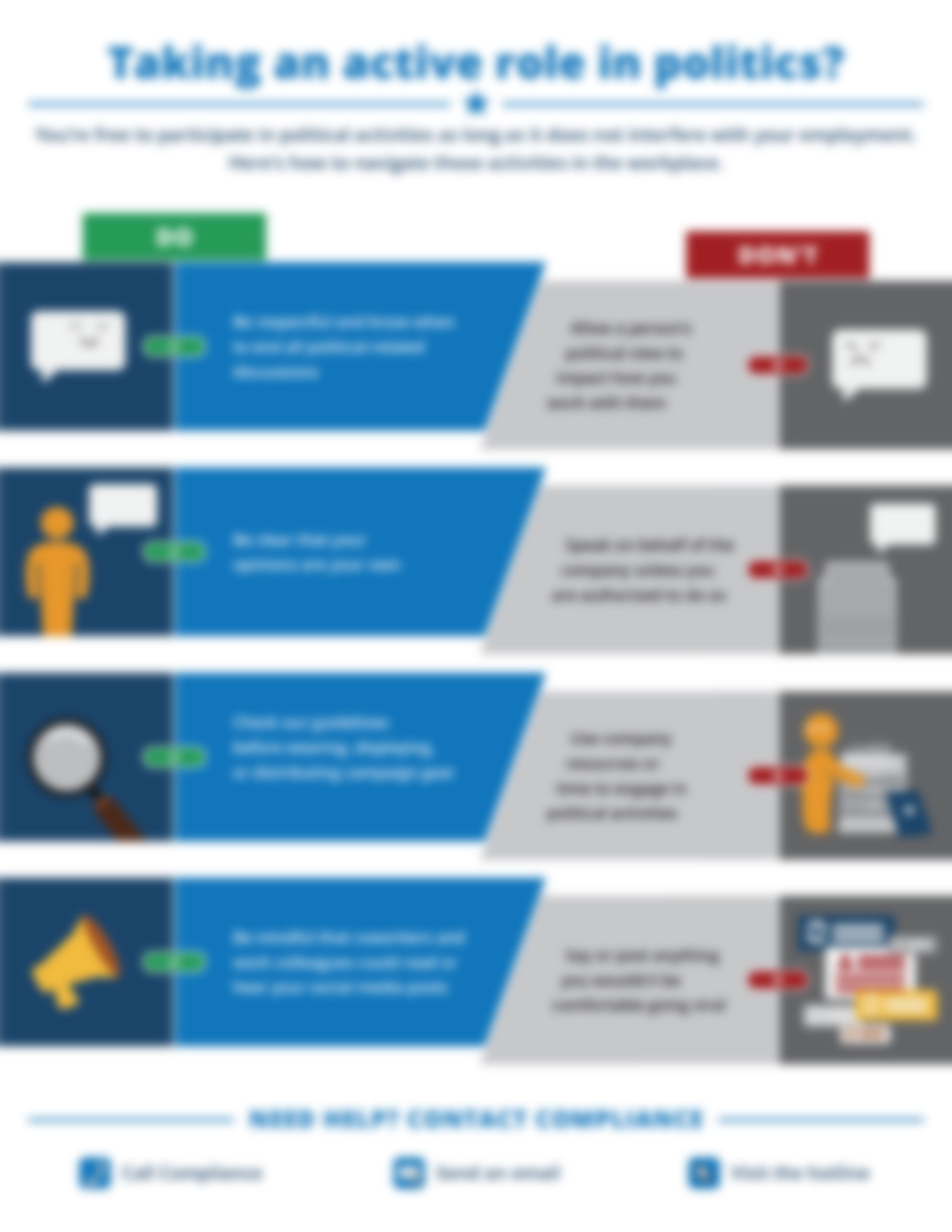
Taking an active role in politics?
Your employees will appreciate this clear guidance on how to participate in political activities without breaking the rules. While political debates are best left to awkward family dinners—let’s face it—personal views are bound to come...
View8✨ -

4 ways bad guys get your password
This is an effective, practical instructor for your employees to keep their passwords—and your company's data—private. We list out the most popular means the crooks use to hack your team’s passwords using fun graphics that help...
View8✨ -

Video: We protect our data
This short, targeted training video (1:27) outlines what counts as data and WHY protecting it matters. It starts off by offering a few examples of what data looks like based on role, goes on to explain WHY protecting this information matters, and...
View10✨ -

Module: Personal Data & Privacy
You don’t expect your employees to memorize everything about privacy and personal data, but that’s the message they’ll get if you dump a ton of regulation-focused material on them. Make it clear that they just need to know the...
View15✨ -

You're free to participate in political activities
It's easy to get carried away during election season. Remind your team that when they're speaking up, they're speaking on behalf of themselves (and using their own resources when doing so).
View2✨ -

Video: Engaging in politics?
Show your teams how to engage in polite political speech with this illuminating video. In less than two minutes (1:25), it shares tips on having healthy discussions and empowers folks to switch topics or end conversations if needed. As for the...
View8✨ -

Vanishing Words: A Guide to Ephemeral Messaging
Ephemeral messaging—aka self-destructing apps—are an easy way to send a quick status update. But, when it comes to business discussions, your employees need to know the DOs and DON’Ts of using these apps to keep your company out of hot...
View6✨ -

Module: Annual Refresher Course
Still stuck doing annual check-the-box training? Gross, and sorry. But hey, at least this 31-slide kit will make it 10 minutes long and actually relevant to every employee. So, you've got that going for you, which is nice. The ideal annual refresher...
View25✨ -

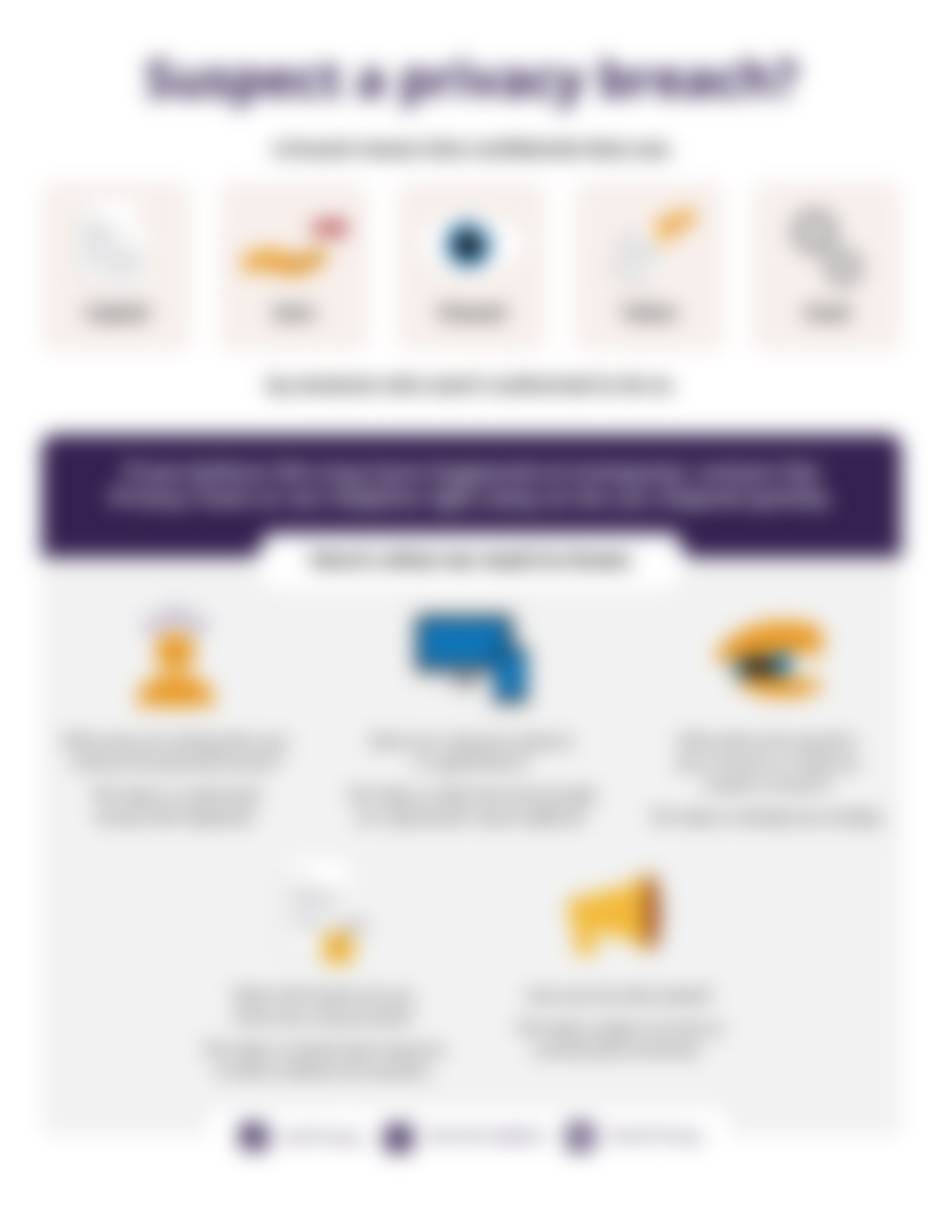
Suspect a privacy breach?
Awkward silence = cringe. Awkward silence with your coworkers = just plain terrible. Help your employees avoid long pauses and staring contests with this incredibly helpful infographic. It covers everything they need to share about a potential data...
View8✨ -

Received a request to transfer data?
What counts as "personal data" to one person might not be to another, which can create major headaches. Use this decision tree to remedy your ills and ensure all your teams have a healthy dose of privacy know-how. In five simple steps, it guides them...
View8✨ -

Use your own resources - horizontal
Remind your team that politics aren't banned at the office, but folks should use their own time and resources when showing political support.
View2✨ -

All expenses must include receipts
Help your people reviewing invoices avoid fraud or bribery by showing them what red flags look like—they'll love you for it! Use these graphics alongside our other invoice red flag pieces for a strategic campaign tackling this compliance priority.
View2✨ -

Expenses must have a clear business purpose
Help your people reviewing invoices avoid fraud or bribery by showing them what red flags look like—they'll love you for it! Use these graphics alongside our other invoice red flag pieces for a strategic campaign tackling this compliance priority.
View2✨ -

Overseas Travel Module
Behold: a simple, immersive way to give your employees detailed guidance on overseas travel risk. It's set up to tie to other parts of your program and pairs well with our travel checklist and a nice pinot. As seen in the video tour of Design Club, this...
View15✨ -

Use your own resources
Remind your team that politics aren't banned at the office, but folks should use their own time and resources when showing political support.
View2✨