Use of Company Assets
-

Video: Careful Communications
Give your teams clear guidance on the do’s and don’ts of virtual communications with this short video (2:15). In less than 3 minutes, this video breaks down the top five things to consider when engaging in virtual communications: the...
View8✨ -

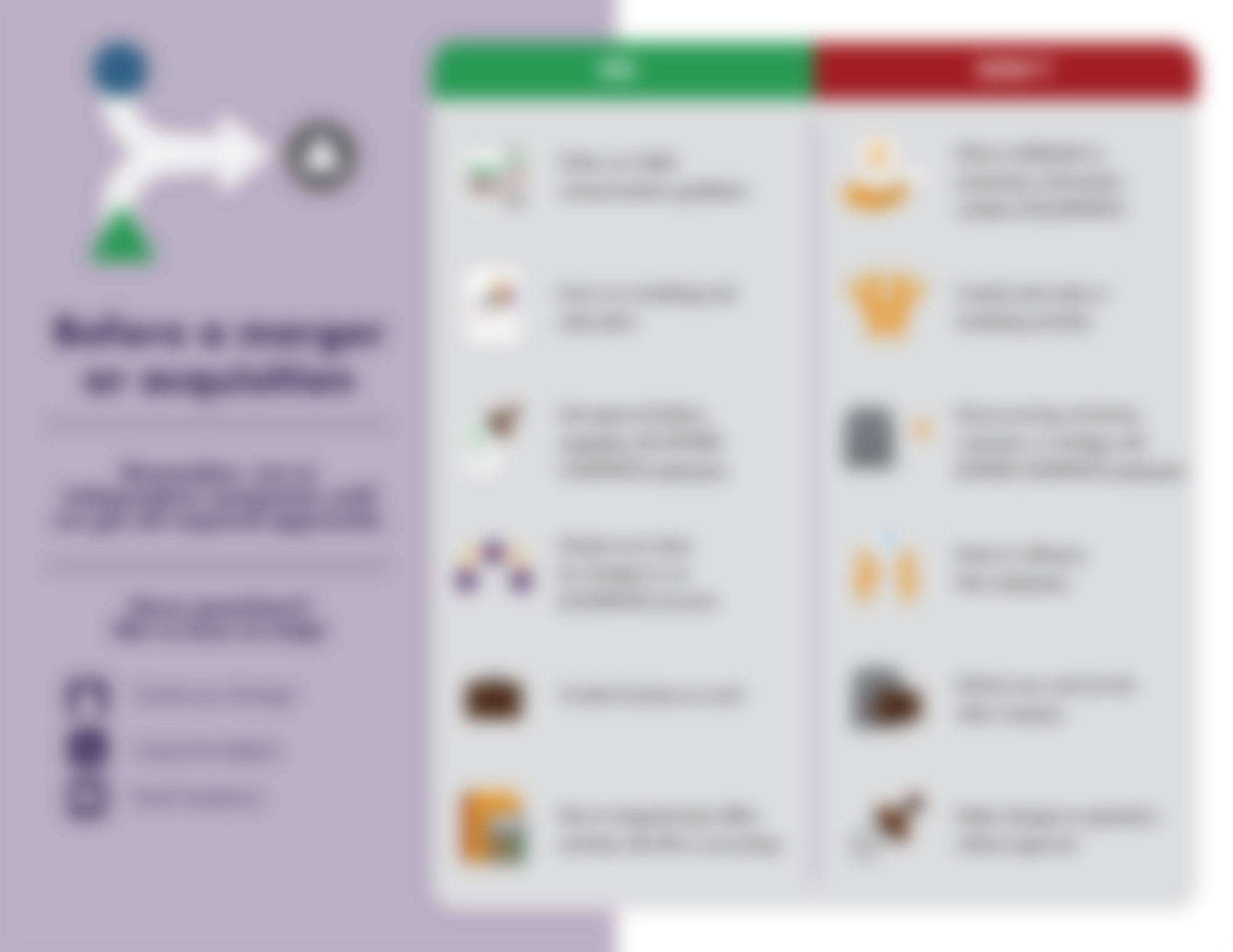
Before a merger or acquisition...
Mergers and acquisitions can be both exciting and terrifying, like base jumping, that long drop on a rollercoaster, or attending a social event for us introverts. While we don’t have a remedy for that weird stomach feeling, we do have a solution to...
View8✨ -

Careful virtual communications (mini-module)
Virtual communication has tons of advantages like convenience and efficiency. But along with these pros come disadvantages like misinterpretation and lack of privacy. In seven brief slides, this deck gives your employees everything they need to...
View8✨ -

Data Processing Agreement checklist
Everyone tells their teams to do their due diligence, but do they know what that actually looks like? This job aid gives your IT and procurement teams the ultimate vendor contract checklist, covering everything from contract basics to data-processing...
View8✨ -

No inappropriate websites at work (phone version) - horizontal
Everyone “knows” they’re not supposed to look at dirty pictures at work—it’s just that they think they can get away with it and it doesn’t impact anyone else. This graphic encourages bystanders (or, here, you know,...
View2✨ -

No inappropriate websites at work (phone version)
Everyone “knows” they’re not supposed to look at dirty pictures at work—it’s just that they think they can get away with it and it doesn’t impact anyone else. This graphic encourages bystanders (or, here, you know,...
View2✨ -

No inappropriate websites at work (desk version) - horizontal
No matter how hard IT tries, you can't block all the porn. Use this messaging to remind people that looking at dirty stuff at work is insanely inappropriate and disrespectful.
View2✨ -

No inappropriate websites at work (desk version)
No matter how hard IT tries, you can't block all the porn. Use this messaging to remind people that looking at dirty stuff at work is insanely inappropriate and disrespectful.
View2✨ -

Submitting a Timesheet?
Getting creative at work is usually a good thing, but not when it comes to timekeeping. Incorporate this checklist into the time tracking process, so both your hourly employees and managers are crystal clear on the rules. This way, small adjustments can...
View8✨ -

Lock it down - horizontal
This simple graphic shows your folks three easy-but-necessary ways to protect your stuff from intruders.
View2✨ -

Harassment: Cyberbullying
“Stop being a jerk on Facebook, Caitlyn.” But like, in a fun campaign format. Using collateral you can print in multiple formats (screensavers, posters, mousepads, and coasters), this campaign drives home the simple message that your company...
View12✨ -

Harassment: Inappropriate Computer Usage
No matter how hard IT tries, you can't block all the porn. Use this messaging to remind people that looking at dirty stuff at work is insanely inappropriate and disrespectful. Everyone “knows” they’re not supposed to look at dirty...
View12✨ -

Travel & expenses training module for managers
This simple visual guide shows your management team how to quickly identify any impermissible expenses prior to approving payment. This visual guide syncs up with our deep-dive travel and expense checklist. Each page expands on one of the 24 checklist...
View15✨ -

Lock it down
This simple graphic shows your folks three easy-but-necessary ways to protect your stuff from intruders.
View2✨ -

Only approve known expenses
Remind your employees that vague details in expense reports aren't harmless—they could be hiding fraud or bribes.
View2✨ -

Protect your password!
Give your folks these simple rules to lock down their passwords—and protect your info.
View2✨ -

Away from your computer?
Make sure your team always remembers: an open computer, left alone, is a privacy breach waiting to happen.
View2✨ -

Laptop get swiped? Report it!
Make sure your folks know that when their tech is stolen, call the company—now.
View2✨ -

Going on a trip? Protect your data!
Show your folks these simple, but vital, rules for keeping company and personal info from being stolen while traveling. It’s not always intuitive that travel creates risk—people lose stuff, they get their computer stolen, hackers target...
View6✨