Cybersecurity
Job aids
Infographics
-

How to use AI Chatbots at work
Your employees are eager to leverage AI chatbots to boost productivity and enhance their work. But how do you balance that with cybersecurity, protecting IP, and reputational risk? While prohibiting the use of AI might sound good, it ignores human...
View6✨ -

We protect our data
Foster a culture of data security at your company with this infographic, which answers the “why” of data protection with four key points: it’s the law, it’s good business, our customers expect it, and it’s the right thing to...
View6✨ -

Notify Privacy when mistakes happen
Being accountable and fixing mistakes yourself is great, but when it comes to privacy mishaps, there are situations where the Privacy Team needs to be looped in. This infographic explains the most common scenarios that require their helping...
View6✨ -

Don't get fooled by email scammers
Successful spear phishing sounds cool, but is one of your cybersecurity team's worst nightmares. Educate your team on the biggest red flags. Using a criminal graphic to grab their attention, this tool vividly highlights the not-always-obvious signs of...
View8✨ -

Get asked to click on a link? (job aid)
Scammers are complicated, but spotting when they're spoofing web domains doesn't have to be. Use this helpful piece to teach your team the basics of avoiding fraudulent payments, misplaced confidential documents, and a compromised network by knowing...
View6✨ -

4 ways bad guys get your password
This is an effective, practical instructor for your employees to keep their passwords—and your company's data—private. We list out the most popular means the crooks use to hack your team’s passwords using fun graphics that help...
View8✨ -

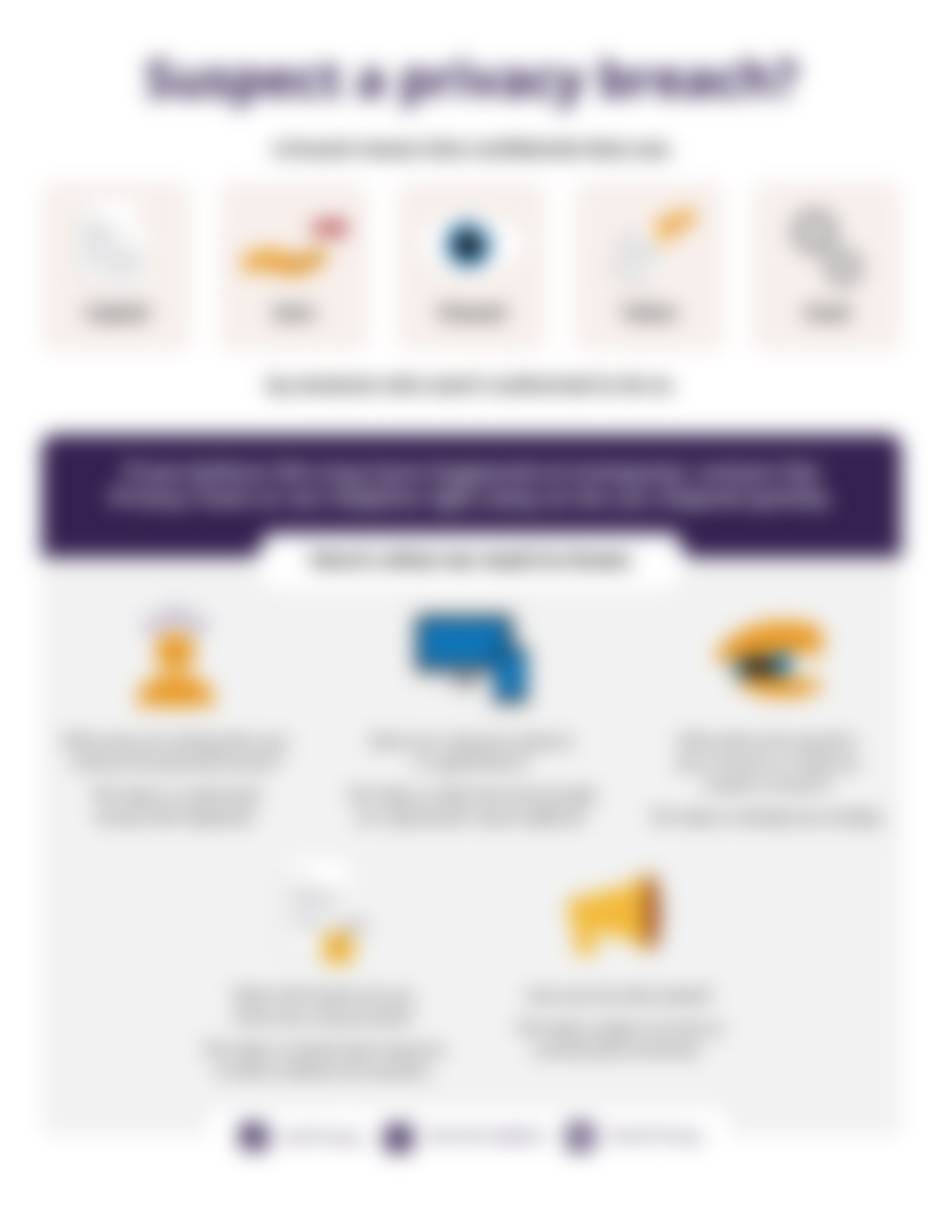
Suspect a privacy breach?
Awkward silence = cringe. Awkward silence with your coworkers = just plain terrible. Help your employees avoid long pauses and staring contests with this incredibly helpful infographic. It covers everything they need to share about a potential data...
View8✨ -

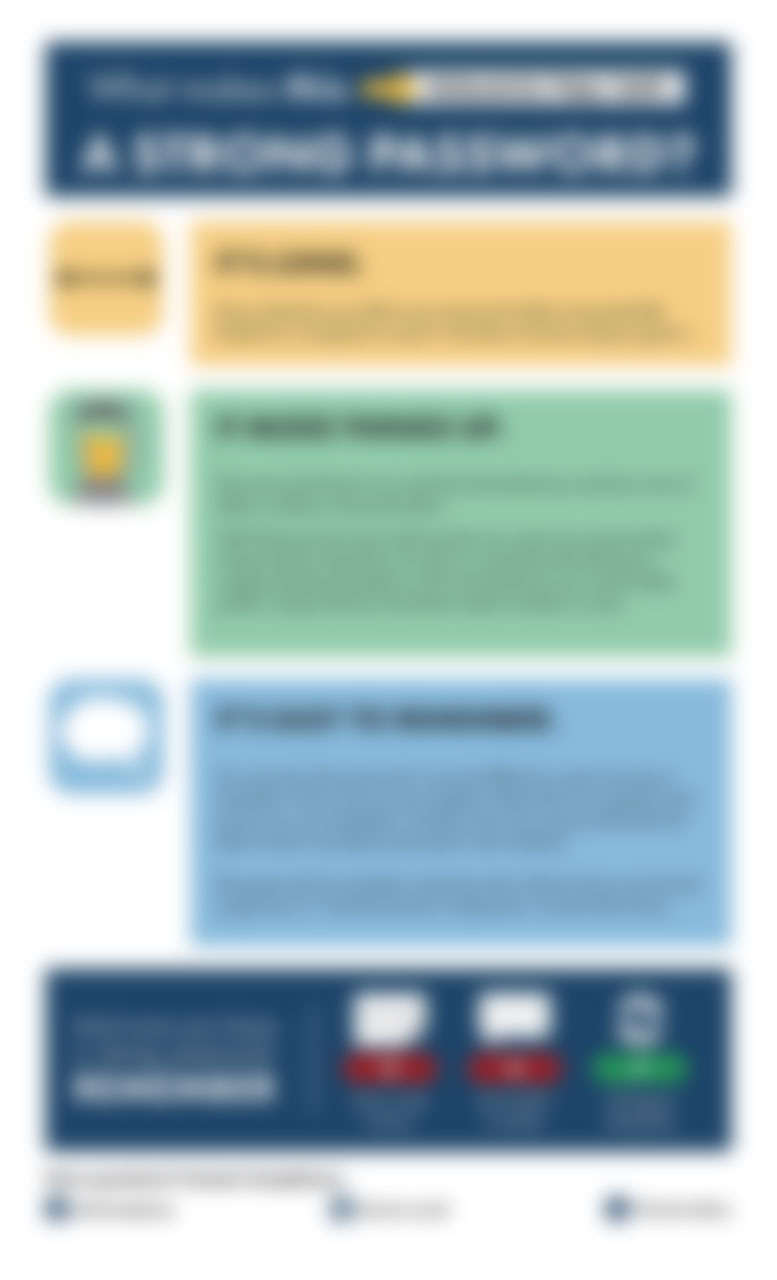
Anatomy of a strong password
Spot the reference to Will Smith in this visual guide for creating safe, strong, and easily remembered passwords. Everyone hates generating a super complicated password, getting a snippy email from IT that they’re overdue to change it, forgetting...
View8✨ -

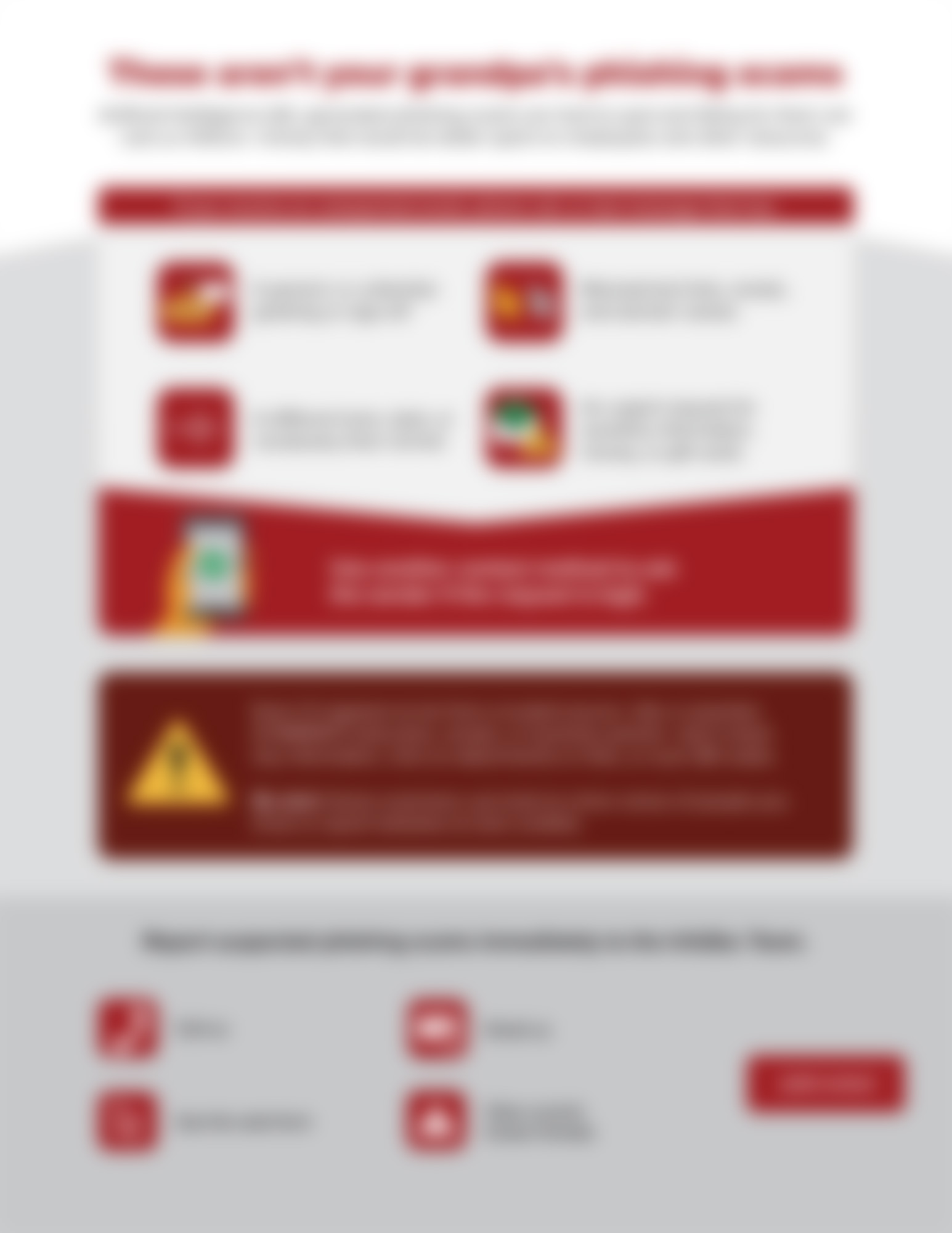
These aren’t your grandpa’s phishing scams
Phishing schemes have become much more advanced and difficult to spot if you don’t know what to look for. So, educate your folks on phishing in the age of AI with this helpful infographic. This at-a-glance tool explains some of the common bait...
View8✨ -

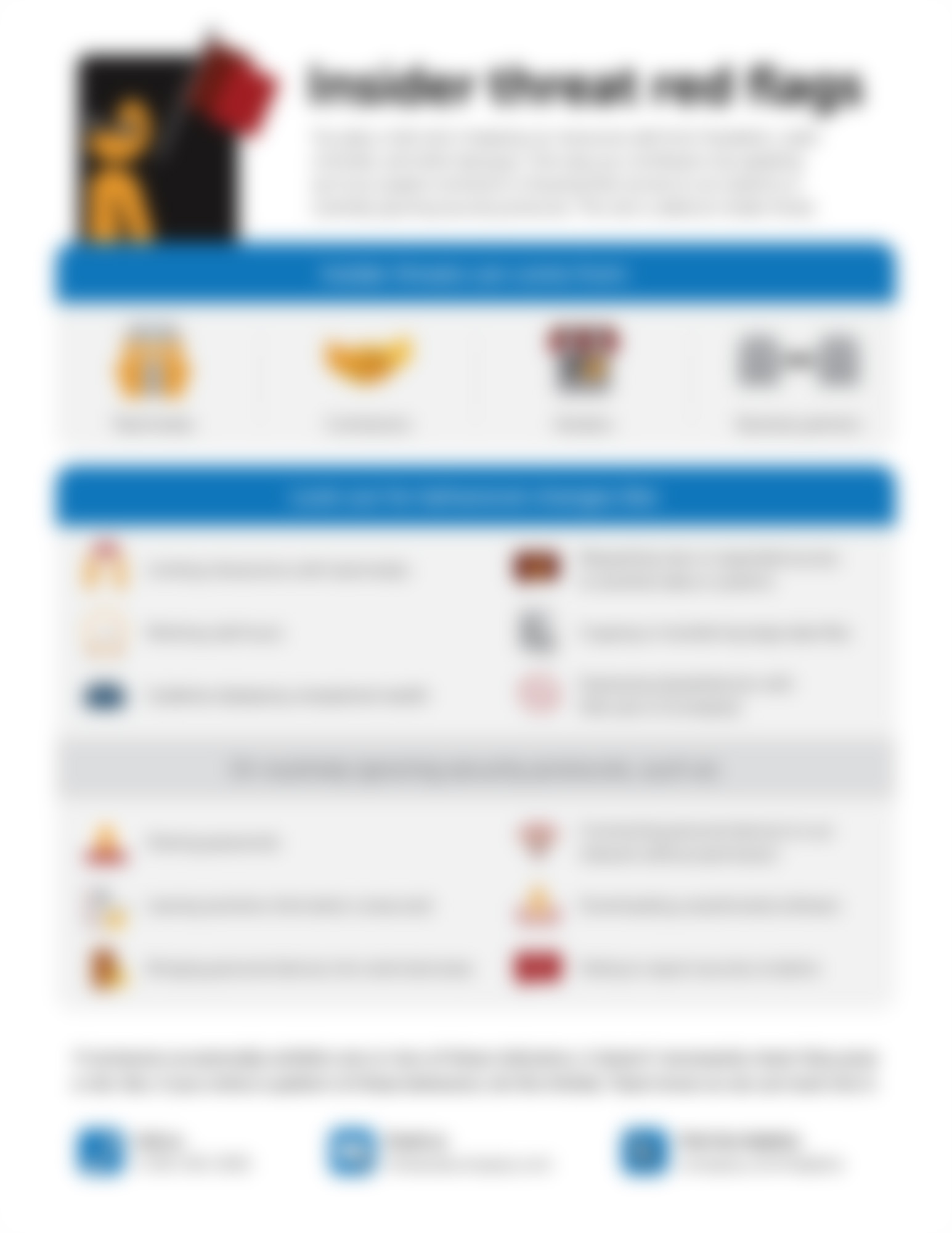
Insider threat red flags
Educate your employees on what insider threats are, where they come from, and some common red flag behaviors. This infographic kicks things off with a not-so-obvious concept: that insider threats don’t necessarily come from inside the...
View8✨ -

How to protect our data from imposters
Kids dressing up as police officers = super cute. Adults impersonating them to get your company’s data = just plain creepy. But do your employees know what to do if they get a strange data request? Use this infographic to highlight who scammers...
View8✨ -

Going on a trip? Protect your data!
Show your folks these simple, but vital, rules for keeping company and personal info from being stolen while traveling. It’s not always intuitive that travel creates risk—people lose stuff, they get their computer stolen, hackers target...
View6✨