Confidentiality
Business Development Team
-
 🔥 Trending
🔥 TrendingPreparing to gather competitive intelligence?
While going undercover and being a super sleuth sounds like fun, it’s not something you want your employees doing to sniff out what your competitors are up to. Use this piece to explain the right way to gather information and what’s totally...
View8✨ -

Insider Trading Basics
Gordon Gekko may think that greed is good, but your company doesn't when it comes to insider trading. Educate your employees on the basics with this graphic piece. Aimed at a general audience, this piece lays out three common categories of material...
View8✨ -
 🔥 Trending
🔥 TrendingWould you trade on it?
This graphic guide simplifies the types of information that should be protected to avoid insider trading. Without getting too far in the weeds of securities terminology (woof), this piece highlights common categories of material non-public...
View6✨ -

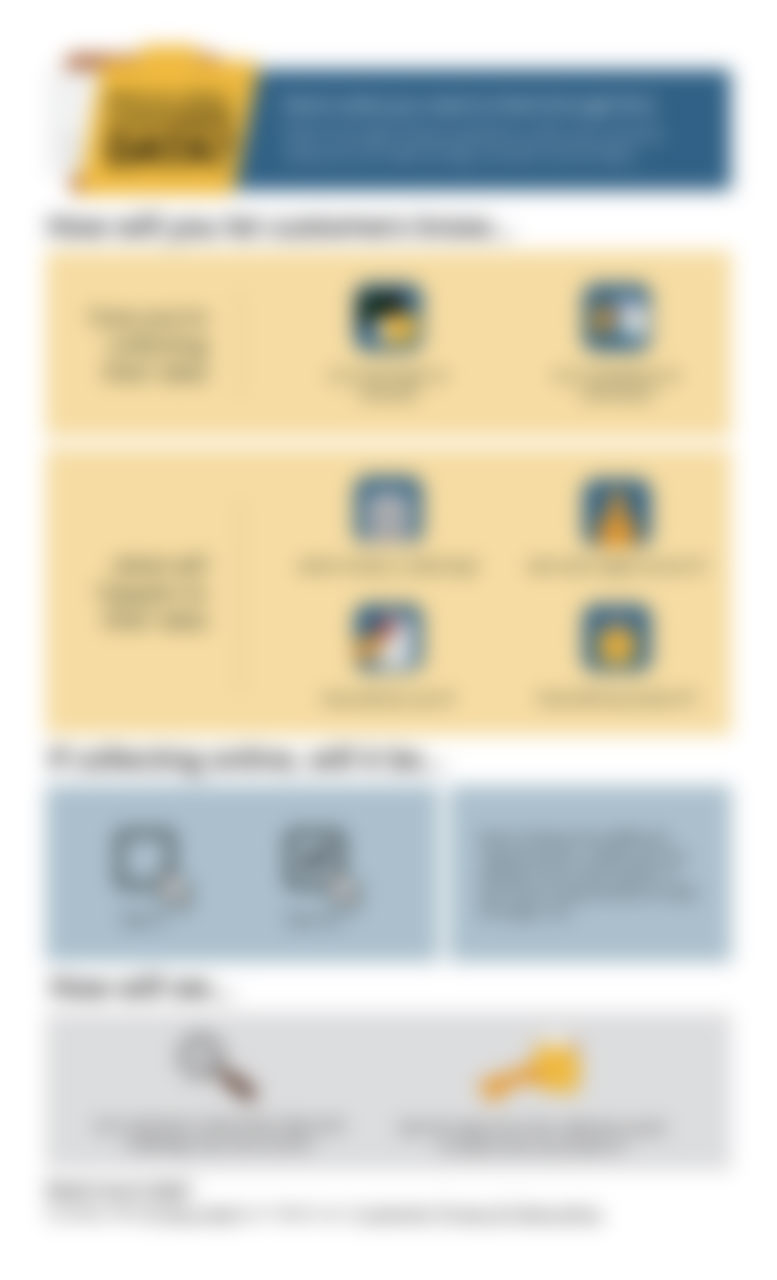
Want to collect customer data?
A handy infographic based on FTC guidance, this walks your teams through the main issues involved in collecting and using customer data. Rather than give hard-and-fast rules, this piece asks critical questions about the use of customer...
View8✨ -
 🔥 Trending
🔥 TrendingHow to tell if someone’s asking for a bribe
Since shady people rarely come out and say, “pay this bribe,” it can be tricky to know when someone’s asking for one. especially when it involves non-monetary favors and sharing information. This clever infographic reveals the five...
View8✨ -

Video: Watch out for red flags from third parties
In this short, targeted training video (1:45), employees will learn what to watch out for when working with third parties. We’ll explain the five main scenarios that are most likely to cultivate red flags, like working with government officials or...
View10✨ -

Module: Personal Data & Privacy
You don’t expect your employees to memorize everything about privacy and personal data, but that’s the message they’ll get if you dump a ton of regulation-focused material on them. Make it clear that they just need to know the...
View15✨ -

Do you know your third parties? - horizontal
When managing third party relationships, clarity is key. This on-point graphic serves as a simple reminder of what things your employees need to be aware of to make sure everyone is on the same page.
View3✨ -

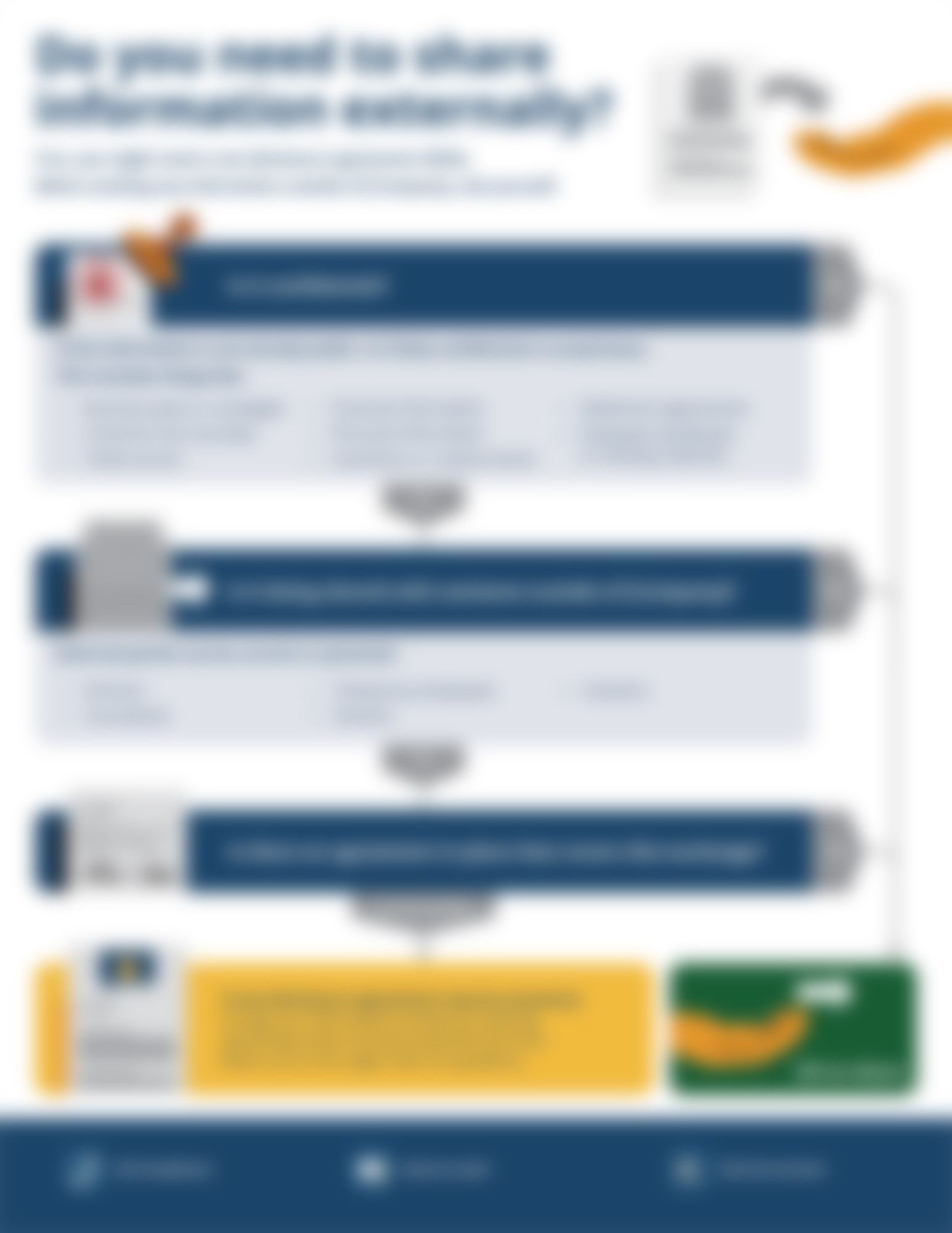
Do you need to get an NDA signed?
Ever wonder if something you're about to share needs to be kept hush-hush? This handy guide is here to help! Think of it like a three-question quiz: answer yes or no, and it'll tell you if a Non-Disclosure Agreement (NDA) is needed before anyone spills...
View8✨ -

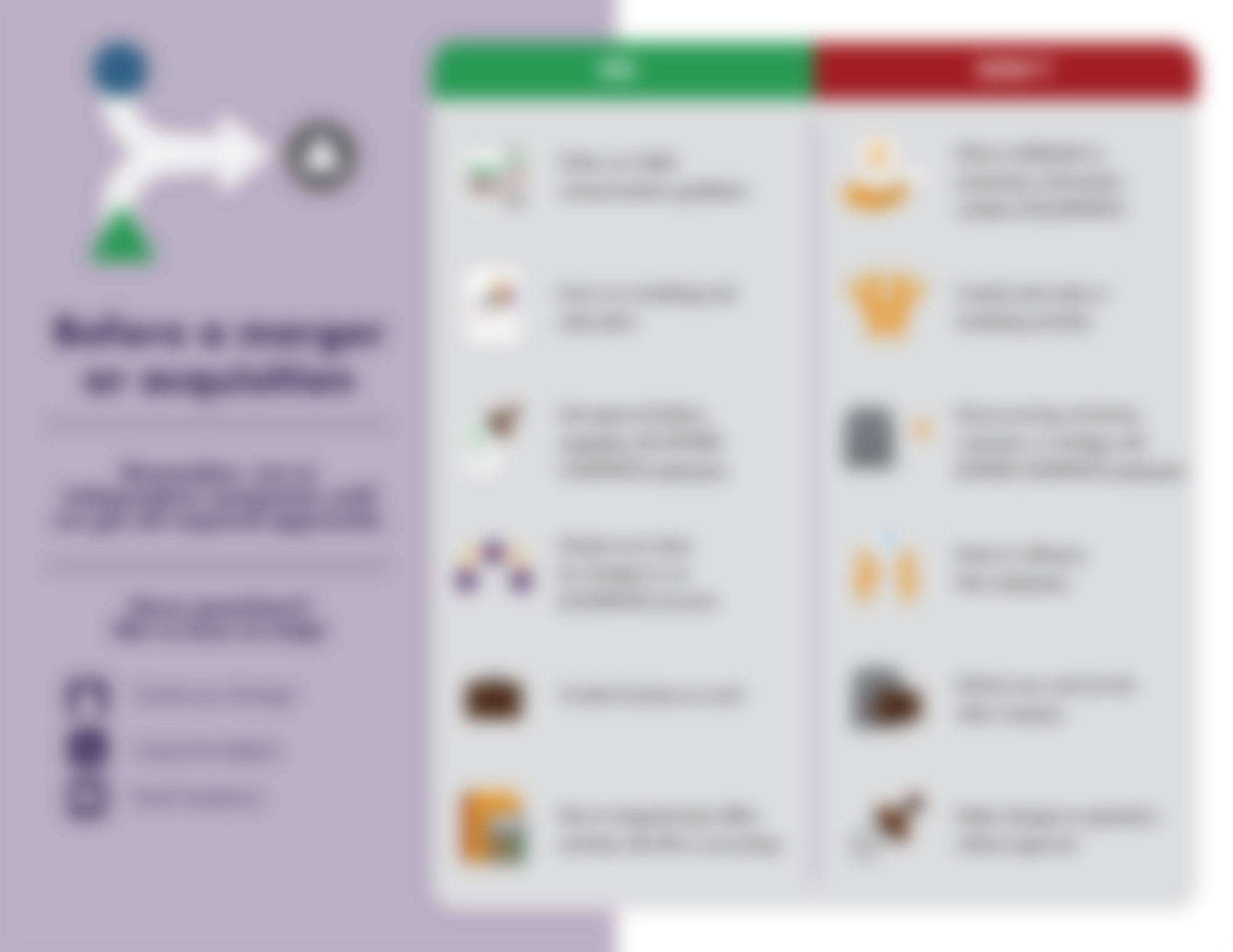
Before a merger or acquisition...
Mergers and acquisitions can be both exciting and terrifying, like base jumping, that long drop on a rollercoaster, or attending a social event for us introverts. While we don’t have a remedy for that weird stomach feeling, we do have a solution to...
View8✨ -

Handling personal data (mini-module)
Give your teams the clarity they need when it comes to handling and managing personal data. In eight brief slides, this deck gives employees an overview of how to identify personal data, then walks them through how to use it, handle it, store it...
View7✨ -

Received a request to transfer data?
What counts as "personal data" to one person might not be to another, which can create major headaches. Use this decision tree to remedy your ills and ensure all your teams have a healthy dose of privacy know-how. In five simple steps, it guides them...
View8✨ -

Social Media for Sensitive Projects
Don’t let your employees give away secret information for free. This handy decision tree shows employees the potential pitfalls of social media use while working on highly confidential matters. Postings pics, tagging coworkers/vendors, checking...
View8✨ -

Third Party Code of Conduct Training
Your third parties—like vendors, consultants, suppliers, and business partners—are essentially an extension of your org, so they need to know and uphold your standards. Share this practical module with them to make sure they get it. In about...
View12✨ -

Interacting with clients and service providers
While treating customers and vendors with respect is the right thing to do, it’s also great for business. Avoid helpline complaints and negative reviews (including on job search sites) by explaining exactly what civility and respect look like when...
View8✨ -

Going on a trip? Protect your data!
Show your folks these simple, but vital, rules for keeping company and personal info from being stolen while traveling. It’s not always intuitive that travel creates risk—people lose stuff, they get their computer stolen, hackers target...
View6✨