Handling Information
-

Working remotely? Protect your data!
Your employees likely work on the go—from hotels, airports, home, bathroom stalls (hey, we don’t judge!)—which invites increased cybersecurity, privacy, and confidentiality risks. Kick your worries to the curb by giving them this tool,...
View8✨ -

Handling Personal Information?
This easy-to-use chart covers what counts as personal information—and how to think through managing it. Handling personal information—whether it’s your customers’ or your own employees’—is risky, so help your...
View8✨ -

Can you throw it away?
Use this elegant decision tree to help your people understand the ifs, whens, and hows of getting rid of documents. Keep versus shred may feel like second nature to your compliance and legal teams, but your other employees often need more guidance. This...
View8✨ -

You might need an export license (ways to export version)
This graphic one-pager shows your team how to spot trade-compliance issues when sharing with non-citizens. Just because you’re not handing it to a courier doesn't mean it’s not an export—but that’s not really intuitive. This...
View8✨ -

You are responsible for what you know - horizontal
Keep your Code of Conduct top-of-mind and aligned with everyday tasks with this graphic. Even better? It's part of an entire system: use it with our Annual Refresher Course and Basic Code of Conduct Obligations infographic for a...
View2✨ -

Is it confidential?
This elegant decision tree helps your team quickly determine if they can share info—or keep it private. One of our favorite pieces, this breaks down the main elements of what constitutes info that should NOT be made public without approval. Even...
View8✨ -

Don't get fooled by email scammers
Successful spear phishing sounds cool, but is one of your cybersecurity team's worst nightmares. Educate your team on the biggest red flags. Using a criminal graphic to grab their attention, this tool vividly highlights the not-always-obvious signs of...
View8✨ -

Travel & expense red flags checklist
Stop fraud and corruption risks in their tracks with this thorough checklist for reviewing T&E reports. Help your managers externalize their memory of procedures and red flags with this piece—they can focus on the harder questions when they...
View8✨ -

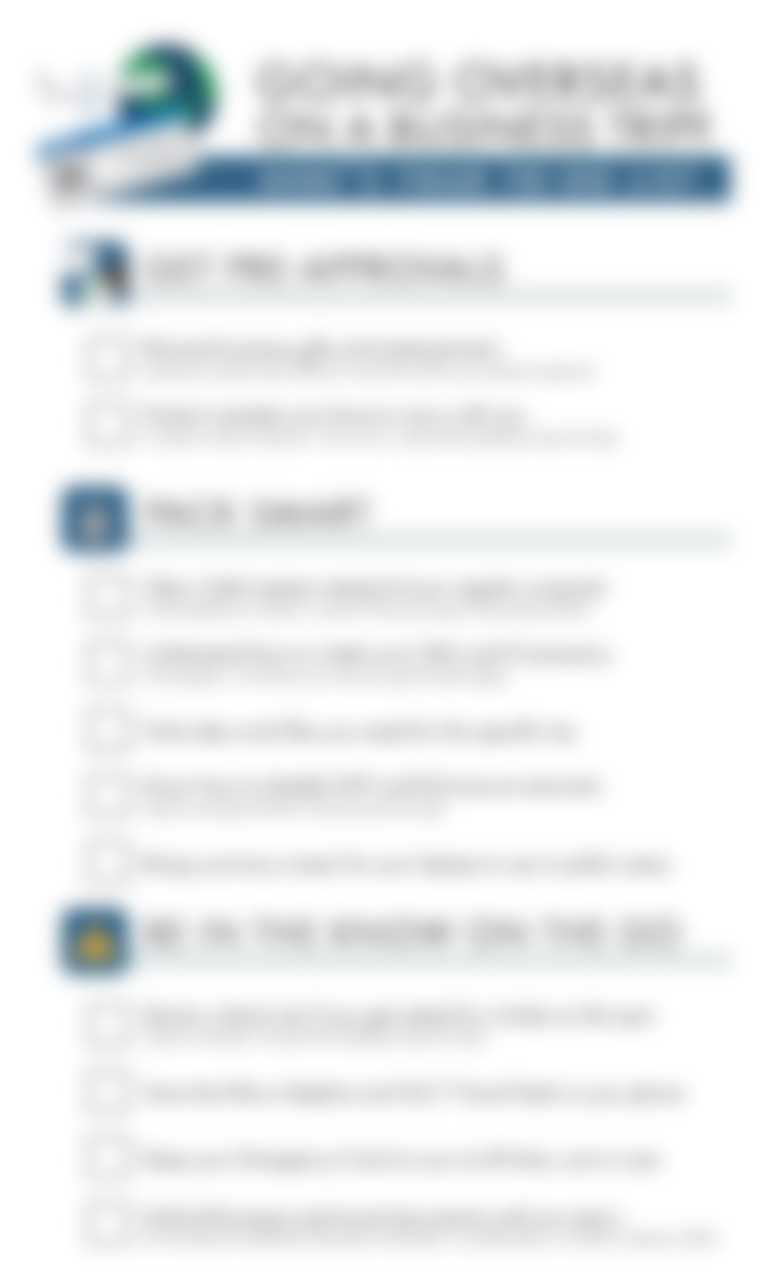
Going on a business trip? (Overseas travel checklist)
This piece is famous for a reason! These simple to-do's prepare your international travelers how to be safe and ethical abroad, without getting mired in legal details. This checklist covers the trade control, cybersecurity, privacy, anticorruption,...
View8✨ -

Get asked to click on a link? (job aid)
Scammers are complicated, but spotting when they're spoofing web domains doesn't have to be. Use this helpful piece to teach your team the basics of avoiding fraudulent payments, misplaced confidential documents, and a compromised network by knowing...
View6✨ -

You might need an export license (deemed exports version)
This easy tool explains the completely non-intuitive concept of "deemed exports" in trade compliance. Focusing on deemed export elements that would surprise most employees, we’ve designed this piece to drive employees to seek help from compliance...
View8✨ -

Template: Visual Legal Hold
Help employees easily understand their obligations when lawsuits happen. When litigation lands, it’s critical that employees know how to navigate a legal hold. Why, then, are so many of them basically unreadable mountains of legalese? Use this...
View8✨ -

4 ways bad guys get your password
This is an effective, practical instructor for your employees to keep their passwords—and your company's data—private. We list out the most popular means the crooks use to hack your team’s passwords using fun graphics that help...
View8✨ -

Check the document retention schedule
People forget that—even if they're finished with a document—your document-retention policy prohibits destroying it. Remind them that your company's policy gives them a handy schedule.
View2✨ -

Conference room combo - horizontal
Gary knows he's supposed to wipe down the whiteboard before kicking on a video call, but he got worked up talking about his Star Wars fanfic that he forgot...and now your engineering data's been leaked. Help all your Garys keep it together with these...
View2✨ -

Confidential? Here's how to handle it - horizontal
Use this effortless graphic to remind your team how to keep your company's confidential info safe.
View2✨ -

Has a government regulator contacted you?
If a regulator reaches out, this guide explains step-by-step who is supposed to do what and when. It’s scary when someone from the government initiates contact, and scared people often don’t make rational decisions—this is an obvious...
View8✨ -

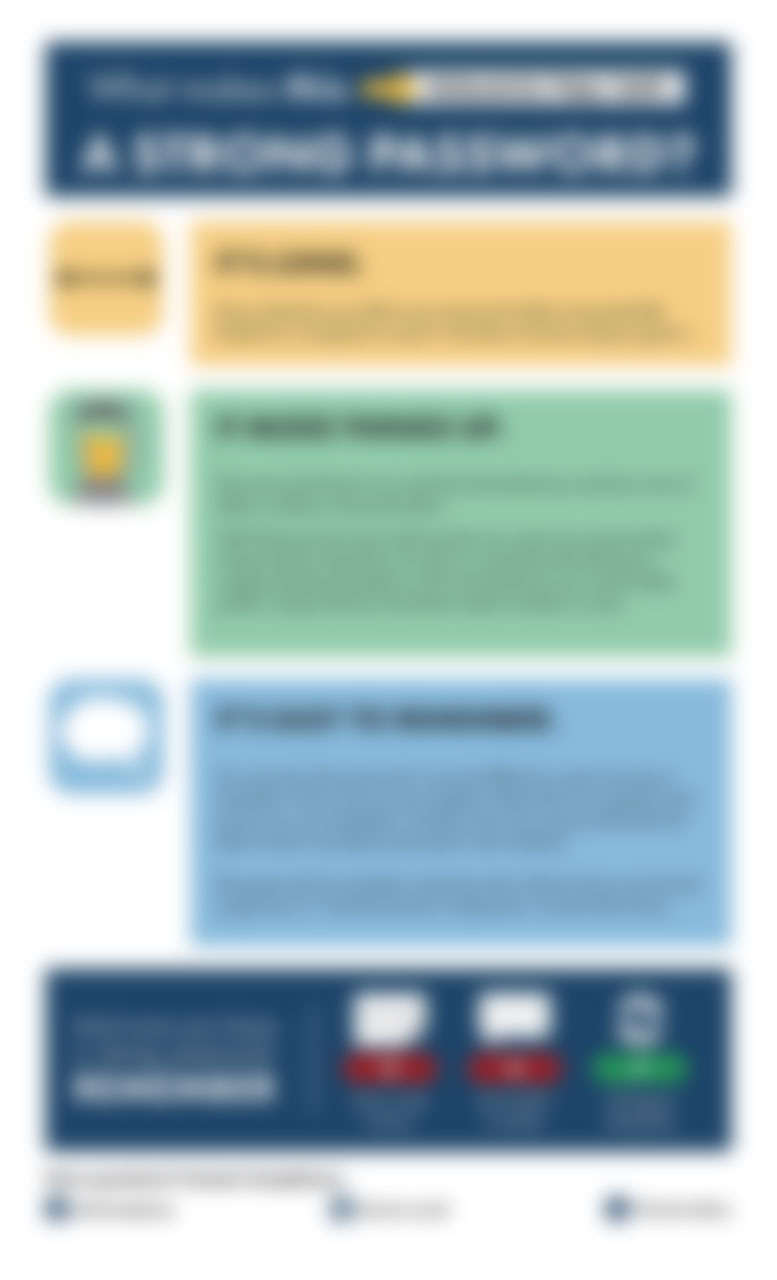
Anatomy of a strong password
Spot the reference to Will Smith in this visual guide for creating safe, strong, and easily remembered passwords. Everyone hates generating a super complicated password, getting a snippy email from IT that they’re overdue to change it, forgetting...
View8✨ -

Confidential? Here's how to handle it
Use this effortless graphic to remind your team how to keep your company's confidential info safe.
View2✨ -

If someone asks for your password, report it!
Prepare your team to be smarter than the scammers by reminding them to never give their passwords over the phone.
View2✨ -

No re-using passwords
Folks hate tough passwords, much less changing them, but ya gotta. This reminds your team to avoid hacking by not reusing work passwords for personal accounts.
View2✨ -

Destroy It Securely
This simple graphic instructs your team that shredding—not the trash can—is how you get rid of docs securely.
View2✨ -

Information been stolen? Report it! - horizontal
Use this straightforward piece to remind your employees that they shouldn't hide when something goes missing, but should raise their hand immediately.
View2✨ -

Shred it! (blue version) - horizontal
It's not hard, but it can be boring. Use this super-graphic piece to remind your team to shred confidential information—each and every time.
View2✨