Welcome to Broadcat’s Compliance Design Club!
Browse our job aids, infographics, red flags checklists, and so many other amazing compliance communications and tools.
-

Working remotely? Protect your data!
Your employees likely work on the go—from hotels, airports, home, bathroom stalls (hey, we don’t judge!)—which invites increased cybersecurity, privacy, and confidentiality risks...
View8✨ -

Can you throw it away?
Use this elegant decision tree to help your people understand the ifs, whens, and hows of getting rid of documents. Keep versus shred may feel like second nature to your compliance and legal teams,...
View8✨ -

Careful virtual communications
We may love dishing about juicy binge-worthy shows on Slack, but it’s easy to forget that these types of communications are on company record, which can lead to problems if discussions take a...
View8✨ -

Don't get fooled by email scammers
Successful spear phishing sounds cool, but is one of your cybersecurity team's worst nightmares. Educate your team on the biggest red flags. Using a criminal graphic to grab their attention, this...
View8✨ -

Get asked to click on a link? (job aid)
Scammers are complicated, but spotting when they're spoofing web domains doesn't have to be. Use this helpful piece to teach your team the basics of avoiding fraudulent payments, misplaced...
View6✨ -

Template: Visual Legal Hold
Help employees easily understand their obligations when lawsuits happen. When litigation lands, it’s critical that employees know how to navigate a legal hold. Why, then, are so many of them...
View8✨ -

4 ways bad guys get your password
This is an effective, practical instructor for your employees to keep their passwords—and your company's data—private. We list out the most popular means the crooks use to hack your...
View8✨ -

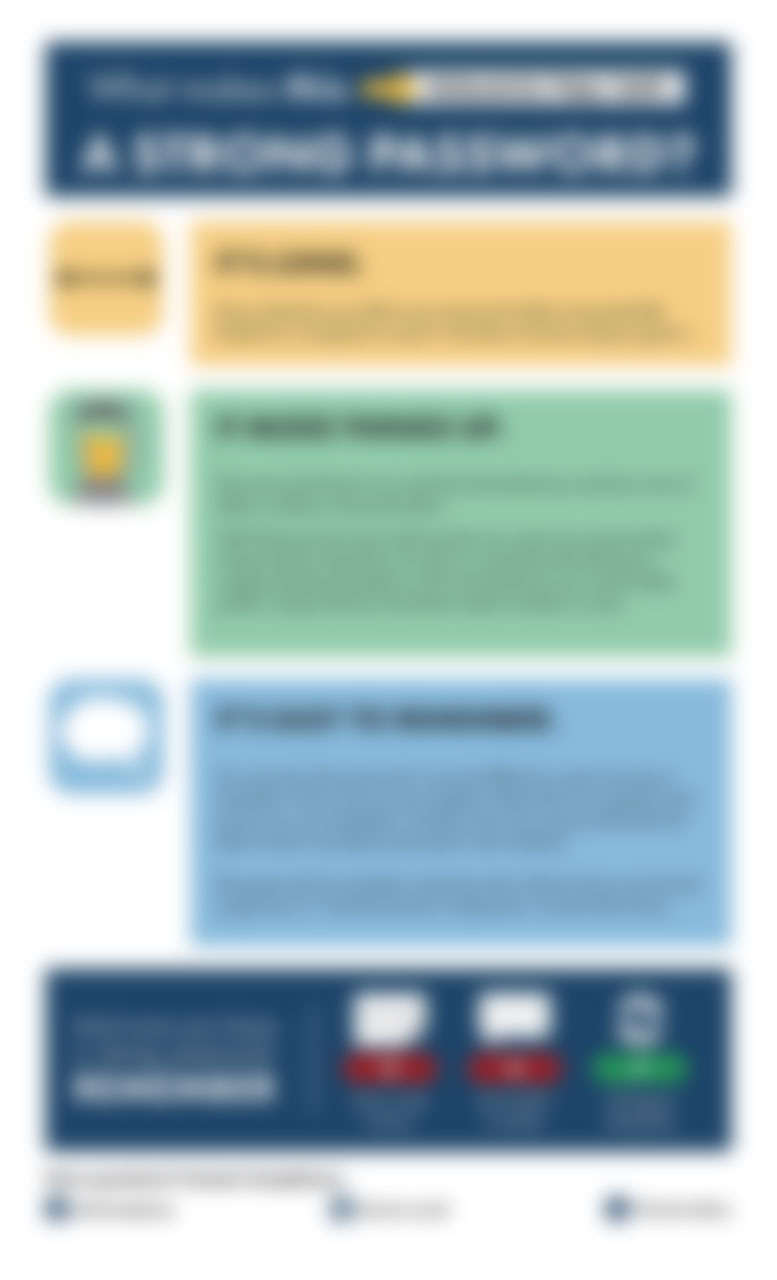
Anatomy of a strong password
Spot the reference to Will Smith in this visual guide for creating safe, strong, and easily remembered passwords. Everyone hates generating a super complicated password, getting a snippy email from...
View8✨ -

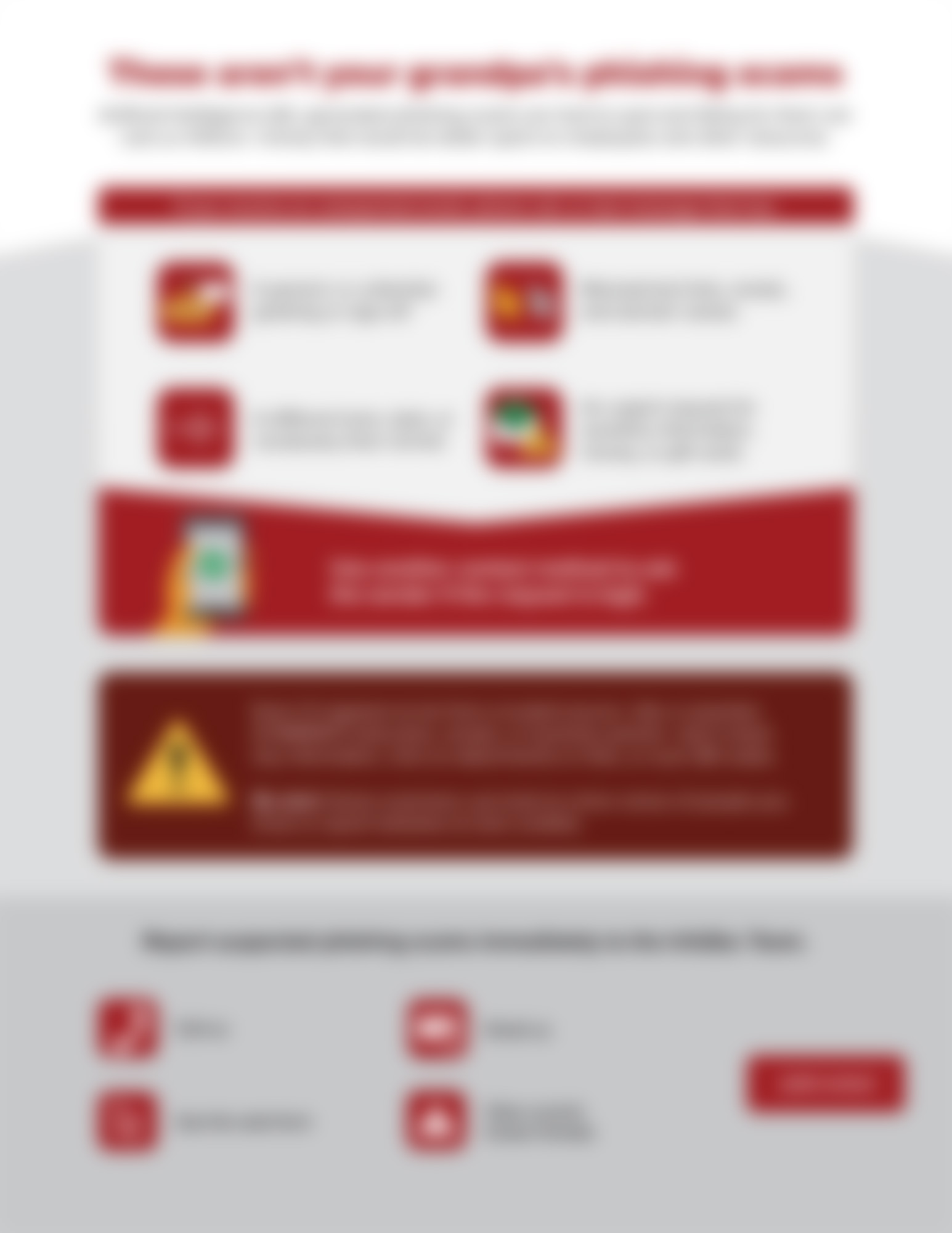
These aren’t your grandpa’s phishing scams
Phishing schemes have become much more advanced and difficult to spot if you don’t know what to look for. So, educate your folks on phishing in the age of AI with this helpful infographic...
View8✨ -

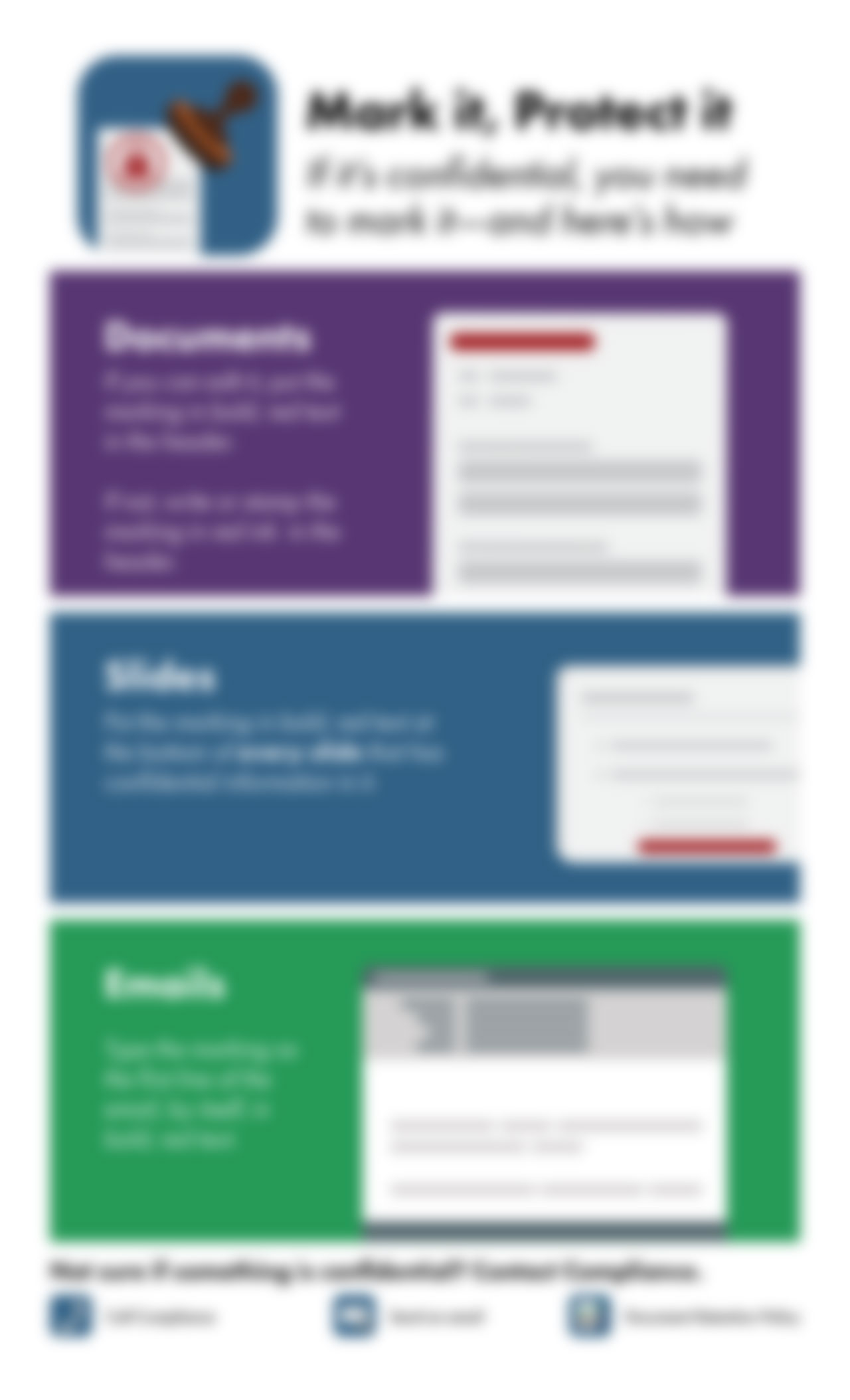
Mark it, protect it
Making sure confidential documents stay private requires some basics. This graphic guide helps your employees keep your info from accidentally getting disclosed by promoting uniformity in marking...
View6✨ -

Respecting Others’ IP
Don’t bore your team with the complexities of intellectual property (IP). Instead, use this delightfully concise infographic to explain it all in simple terms without overwhelming. Whether...
View6✨ -

Submitting a Timesheet?
Getting creative at work is usually a good thing, but not when it comes to timekeeping. Incorporate this checklist into the time tracking process, so both your hourly employees and managers are...
View8✨ -

Going on a trip? Protect your data!
Show your folks these simple, but vital, rules for keeping company and personal info from being stolen while traveling. It’s not always intuitive that travel creates risk—people lose...
View6✨