Handling Information
-

Is it confidential?
This elegant decision tree helps your team quickly determine if they can share info—or keep it private. One of our favorite pieces, this breaks down the main elements of what constitutes info that should NOT be made public without approval. Even...
View8✨ -

Don't get fooled by email scammers
Successful spear phishing sounds cool, but is one of your cybersecurity team's worst nightmares. Educate your team on the biggest red flags. Using a criminal graphic to grab their attention, this tool vividly highlights the not-always-obvious signs of...
View8✨ -

Careful virtual communications
We may love dishing about juicy binge-worthy shows on Slack, but it’s easy to forget that these types of communications are on company record, which can lead to problems if discussions take a sensitive turn. At best: cringey embarrassing...
View8✨ -
 🔥 Trending
🔥 TrendingTravel & expense red flags checklist
Stop fraud and corruption risks in their tracks with this thorough checklist for reviewing T&E reports. Help your managers externalize their memory of procedures and red flags with this piece—they can focus on the harder questions when they...
View8✨ -

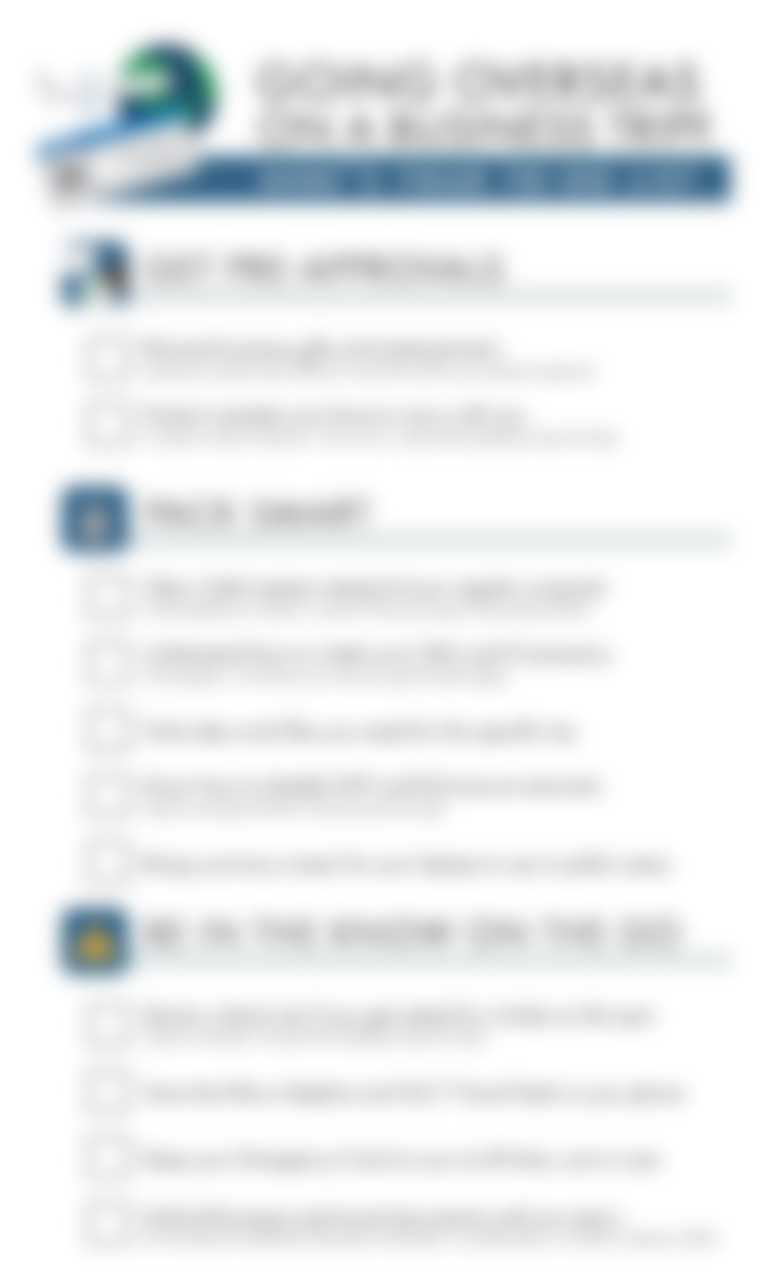
Going on a business trip? (Overseas travel checklist)
This piece is famous for a reason! These simple to-do's prepare your international travelers how to be safe and ethical abroad, without getting mired in legal details. This checklist covers the trade control, cybersecurity, privacy, anticorruption,...
View8✨ -

Would you trade on it?
This graphic guide simplifies the types of information that should be protected to avoid insider trading. Without getting too far in the weeds of securities terminology (woof), this piece highlights common categories of material non-public...
View6✨ -

When should I contact the Privacy Team?
Living your values means ensuring data privacy throughout your org. You’ve written all the policies, operationalized training, and have a Chief Privacy Officer. But do your people know when to pick up the phone and contact the Privacy Team? This...
View8✨ -

Is this personal data?
Maintaining customer and employee privacy has always been important, but with GDPR, CCPA and other privacy regs across the globe, not only is it important—it’s also the law. Ensure your teams know what qualifies as “personal data”...
View8✨ -

Your post may self-destruct, but copies last forever - horizontal
Just because a post is "self-destructing" doesn't mean they can't be shared by others. Remind your folks to be mindful of what they share, even if they think it won't live on.
View2✨ -

Get asked to click on a link? (job aid)
Scammers are complicated, but spotting when they're spoofing web domains doesn't have to be. Use this helpful piece to teach your team the basics of avoiding fraudulent payments, misplaced confidential documents, and a compromised network by knowing...
View6✨ -

Finalizing, Submitting, or Storing Company Records?
This simple checklist helps employees keep good records without getting bogged down with trying to remember what to do. It’s easy to forget how vital recordkeeping is, but sometimes the mere act of insufficient documentation is itself a violation...
View6✨ -

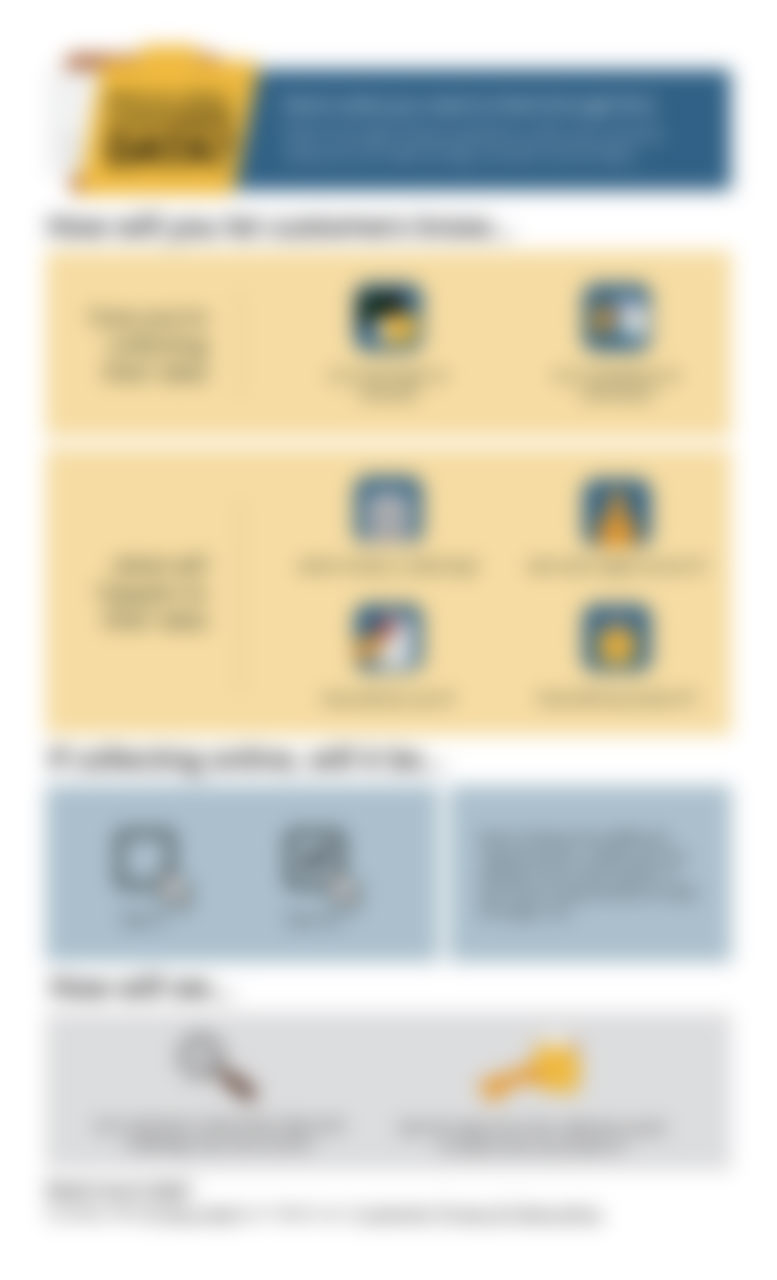
Want to collect customer data?
A handy infographic based on FTC guidance, this walks your teams through the main issues involved in collecting and using customer data. Rather than give hard-and-fast rules, this piece asks critical questions about the use of customer...
View8✨ -

Conflicts of Interest (line art version)
Make sure your employees know what's a conflict of interest—and, just as important, what to do about it. It’s too easy for folks to just “go with their gut” about potential conflicts. This piece uses simple icons to explain when...
View8✨ -

You're free to participate in political activities - horizontal
It's easy to get carried away during election season. Remind your team that when they're speaking up, they're speaking on behalf of themselves (and using their own resources when doing so).
View2✨ -

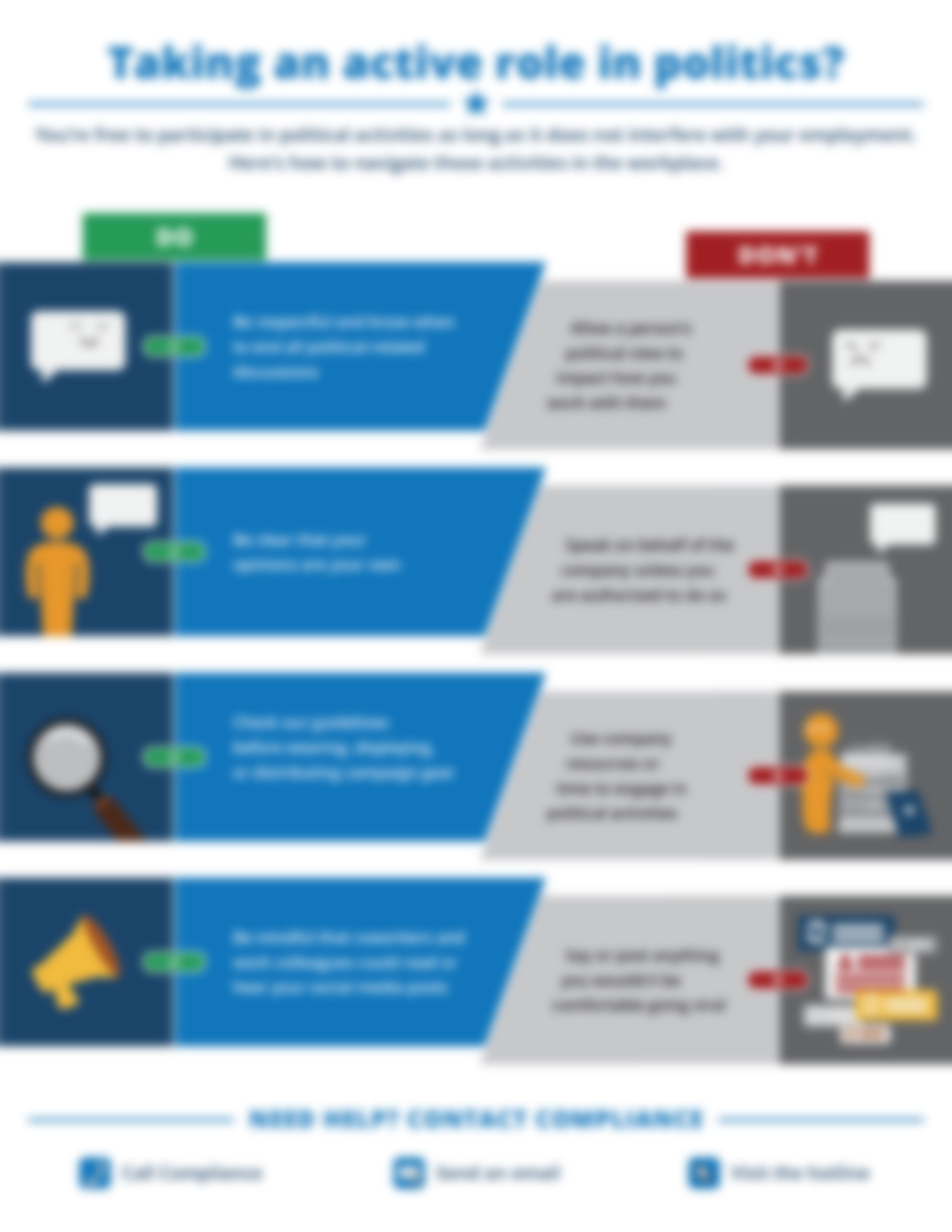
Taking an active role in politics?
Your employees will appreciate this clear guidance on how to participate in political activities without breaking the rules. While political debates are best left to awkward family dinners—let’s face it—personal views are bound to come...
View8✨ -

Dawn Raid: How to Respond
Dawn Raids can be scary, but Happy Cloud knows what to do. Educate your team on how to respond when government agents come knocking. Your team shouldn’t be unprepared for a surprise visit from regulators. This piece offers some tried-and-true...
View6✨ -

Posting on politics?
Help your employees navigate the implications of politics and social media without infringing on their autonomy. Folks wanting to engage in political discussions online can create serious problems for your company. Provide them with an easy flowchart to...
View6✨ -

4 ways bad guys get your password
This is an effective, practical instructor for your employees to keep their passwords—and your company's data—private. We list out the most popular means the crooks use to hack your team’s passwords using fun graphics that help...
View8✨ -

Video: AI Chatbots
Your employees are eager to leverage AI Chatbots—and while having robots help us work is cool, it also poses some serious risk. Help them understand how to use AI Chatbots without introducing a whole host of risks with this easy to digest...
View8✨ -

Video: We protect our data
This short, targeted training video (1:27) outlines what counts as data and WHY protecting it matters. It starts off by offering a few examples of what data looks like based on role, goes on to explain WHY protecting this information matters, and...
View10✨ -

What not to discuss during a merger
Joining forces is exciting, but jumping the gun and prematurely sharing confidential information is not (because, you know, the law). Give this infographic to your employees at the onset of a merger or acquisition so they know what convos are off limits...
View6✨ -

Video: Attending a conference?
Prepare your employees to avoid the risks associated with attending external events using this short, targeted training video (1:20). In 80 seconds, your folks will know which conversation topics are off-limits, how to trust their gut when it comes to...
View7✨ -

What are side letters?
Packing sandwich condiments on the side reduces risk (of mushy bread, bleh!), but contract terms on the side only increases it. Use this checklist to make sure your teams don't spoil the deal! Perfectly proportioned, it starts with a short, but...
View8✨ -

Video: Watch out for red flags from third parties
In this short, targeted training video (1:45), employees will learn what to watch out for when working with third parties. We’ll explain the five main scenarios that are most likely to cultivate red flags, like working with government officials or...
View10✨